Most wallets contain a lot of sensitive information you don’t want in the wrong hands. This can include your driver’s license with your full name, birthday, and your social security number. Of course, credit cards are the first target for most identity thieves, but much more damage can be done with your personal details, especially your social security number. One of our writers, who was an identity theft victim, has written about his first-hand experience and shared his credit protection tips. And today we’ll take a look at some of the steps you should take to help avoid ID theft and fraud from happening in the first place.
What Identity Thieves Do
Identity thieves try to obtain your sensitive information in the following ways.
Stealing mail correspondence from banks or credit card companiesSnatching a wallet or purse in public placesTaking laptops or tablets from an internet cafe or librarySending phishing emails to obtain your bank or credit card login detailsHacking into your computer to pull personal documents with private details
Once these criminals get access to your information, they use it in a variety of ways. The end goal is to somehow obtain money, but the path thieves take to get access to money is different depending on the type of information they can steal from you.
Bank Account: With your login details, your routing and account number is accessible. Criminals can use that information to do direct bank transfers to their own bank account or a criminal shadow business used to funnel stolen funds.Bills: The most common target when stealing your mail is your credit card number. Credit card numbers can be used to make massive online purchases, most commonly for untraceable gift cards.License: Identity thieves can obtain your birthday and your social security number. With this information, they can apply for credit, or even worse apply for official identity documents (like welfare benefits) under your name. Criminals could also file a tax return in your name and steal your tax return check.Health Insurance Cards: Thieves can use your health insurance card and a fake ID to obtain medical care, with the bills going to you.
How to Stop Identity Thieves
Thankfully, you have lots of technology at your disposal to thwart identity thieves. If you consider all of the areas listed above that give identity thieves access to your sensitive information, the technology you use needs to protect every one of those areas.
Computer Security
Since your computer is one of the most common avenues criminals use to obtain your personal information, there are several ways you can use technology to block those identity thieves.
Antivirus: If you do store sensitive documents like tax or bank records on your computer, it’s critical that you keep hacker’s hands off those documents. Installing effective antivirus software is your first line of defense. Never go without, and make sure you’ve scheduled security scans frequently.Offline Storage: A better approach would be to store any sensitive documents on an external storage device, like an external hard drive. This way, even if your computer is ever compromised, hackers wouldn’t have access to any critical information.Malware Scans: If you browse the internet a lot, the odds are you’ve clicked on the occasional ad. Most online ads are benign and safe, but some are set up simply to get adware or malware onto your computer. Antivirus software doesn’t always catch these kinds of issues, which is why running malware scans are so important as well.
Email Security
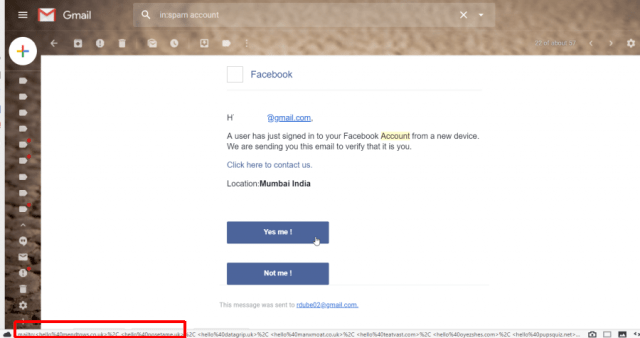
Another very common route identity thieves take to steal your information and your identity is email phishing. There are a number of things you can do to better protect yourself from these kinds of attacks.
Watch Those URLs: When you receive spam mail from criminals who use phishing, those email look authentic. Usually, they’ll appear to come from your bank or credit card company, and try to tempt you to click a link to log into your account. However, you can check those URLs by keeping an eye on the actual URL at the bottom left of the browser window. Always make sure the link goes to the actual company website.
Anti-Phishing Extensions: Beyond watching how you click when you’re reading emails, you can also take advantage of extensions available for your email client to make that much easier. For example, Gmail offers a Chrome extension called Password Alert that alerts you when you’re entering your login details into a site that isn’t authentic.Avoid Clicking: The simplest approach to stopping hackers from stealing your information through email phishing is adopting a policy of never clicking on login links in an email at all. Instead, open a browser tab and go directly to the site to log in instead.
Secure Your Online Accounts
And an even more important step to protect your accounts and passwords is to use Two-Factor Authentication (2FA) on every site it’s available. And while even 2FA can be compromised, it’s the exception and not the rule. For more on how 2FA words and the major sites that provide it, read our 2FA Guide.
Internet Security
Beyond email, you need to protect yourself from identity thieves every time you connect to the internet. There are two main paths that are the weak points when you get online. One is your home’s internet router, which is essentially your gateway to the internet. The other is when you connect to the internet at locations outside your home. Public Wi-Fi networks are a very common target for identity thieves. This is because many of these networks transmit information from your computer to the internet through insecure, open networks.
Lock down your Router: If you don’t believe there could be a hacker parked nearby your house, trying to connect to your home router, you may be surprised one day when that actually happens. Don’t take any chances. Make sure to change the admin password of your router to something other than the default, and enable the router’s external firewall.
Use a VPN on public networks: Public networks are one of the most dangerous ways to connect to the internet. Not only could there be a hacker using a computer on the same network, scanning for other vulnerable, connected systems. But traffic on those networks is usually not encrypted, making everything you transmit over it accessible by other systems. The best way to prevent this is by always connecting to a VPN from these networks before connecting to any website.
Credit Cards
Credit cards are always the first target for criminals because it’s one of the easiest ways to steal money from victims. Criminals usually snatch credit cards from cars or stolen wallets and purses. They then immediately purchase gift cards at stores or make multiple online purchases before you ever realize the cards are missing. Thankfully there are many ways you can use technology to protect yourself from these criminals.
Opt-in for fraud alerts: With the rise of hacking attacks every year, banks and credit card companies now offer customers a free service which will alert you immediately to any suspected fraudulent activity on your account. Take full advantage of those services.Check your credit report every year: The Federal Trade Commission has made free credit reports to everyone in the country. These reports are available once every 12 months. This is offered at a website called annualcreditreport.com. Request your report and review it for any activity you don’t recognize.
Use digital payment systems rather than credit cards: Leave your credit cards at home and remove any risk of them getting stolen. There are lots of digital wallets you can now use at many stores, including Apple Pay, Samsung Pay, or Google Wallet.
Snail Mail Security
It’s difficult to imagine that there are people who would actually rifle through trash just to steal documents that might have sensitive information on it. But that’s exactly what happens every day. Paper documents are one of the most insecure methods for sending information. They are too easy to steal either in transit on the way to your mailbox, or after you’ve thrown them out in the trash. But even with paper documents, there are ways to protect yourself.
Shred all documents: Since your bills and other paper documents are a risk the moment they enter your trash bags and hit the curb, never send them out in the first place. Shred all documents before tossing them.Switch to digital bills: Even better than shredding bills is to never receive them in the first place. Most companies now offer customers the opportunity to switch to digital statements. Not only does it reduce your risk, but it cuts down on wasted paper as well.
Freeze Your Credit Accounts
The ultimate way to stop anyone from applying for credit cards under your name is by freezing your credit report with the three credit bureaus. Each credit bureau offers a page where you can freeze your credit report:
EquifaxExperianTransunion
Once you set a freeze on your report, no one (including you) can apply for credit using your social security number. You can unfreeze your credit temporarily from the three bureaus should you ever need to apply for credit in the future, however. Taking your identity security seriously in today’s modern technical age is critical. Unfortunately, it isn’t a matter of if your personal information will fall into the wrong hands. It’s a matter of when.
![]()